Nikto – WebAPP Penetration Testing Tool
Nikto is web server scanner which performs comprehensive tests against web servers for multiple items, including over 6500 potentially dangerous files/CGIs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be automatically updated.Nikto basically support two scanning modes. Nikto is a Perl language development of open source code, powerful WEB scanning evaluation software, a variety of web server security projects to test the scanning software.
The
vulnerability scanner discovers various issues that are potential
security problems for your web server. The types of issues Nikto can
identify are:
- Fingerprint the web server type and version
- Report old versions of server software if it contains known vulnerabilities
- Discover web server configuration problems (directory listing, backup files, old configuration files, etc)
- Identify specific web applications that are running on the web server
- Check for known application vulnerabilities
nikto -update #Directly update the database
nikto -list-plugins #Plugin list
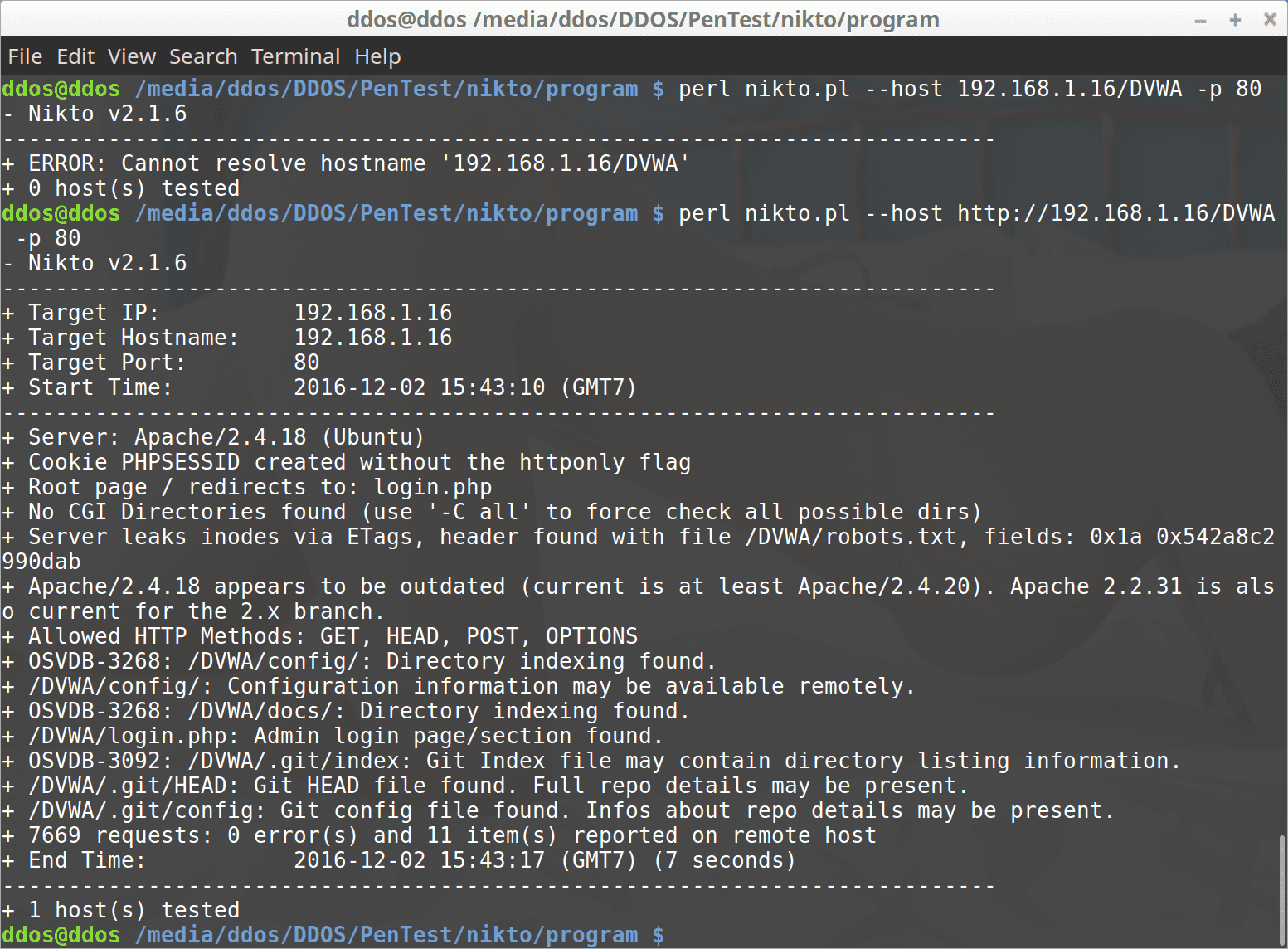
nikto -host http://192.168.1.16/DVWA/ #Specifies the site directory scan
nikto -host 192.168.1.1.109 -port 80,443 #Multiple ports can be specified
nikto –host target.txt #scanning multi target
nmap -p80 192.168.1.1/24 -oG – | nikto -host – #Combined with nmap, on a network segment of the open 80-port host scan
nikto –host https://securityonline.info -useproxy http://localhost:8080 #use proxy on your scanning
Interact with scanning mode
Scan tuning:
1 Interesting File / Seen in logs
2 Misconfiguration / Default File
3 Information Disclosure
4 Injection (XSS/Script/HTML)
5 Remote File Retrieval – Inside Web Root
6 Denial of Service
7 Remote File Retrieval – Server Wide
8 Command Execution / Remote Shell
9 SQL Injection
0 File Upload
a Authentication Bypass
b Software Identification
c Remote Source Inclusion
d WebService
e Administrative Console
x Reverse Tuning Options (i.e., include all except specified)
Encoding technique:
1 Random URI encoding (non-UTF8)
2 Directory self-reference (/./)
3 Premature URL ending
4 Prepend long random string
5 Fake parameter
6 TAB as request spacer
7 Change the case of the URL
8 Use Windows directory separator (\)
A Use a carriage return (0x0d) as a request spacer
B Use binary value 0x0b as a request spacer
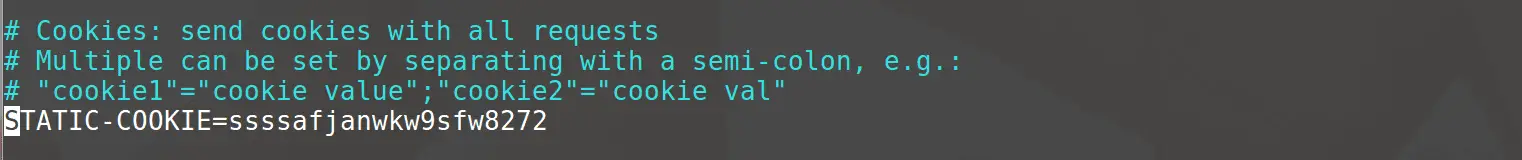
You can configure nikto.conf
- Supports specified cookies
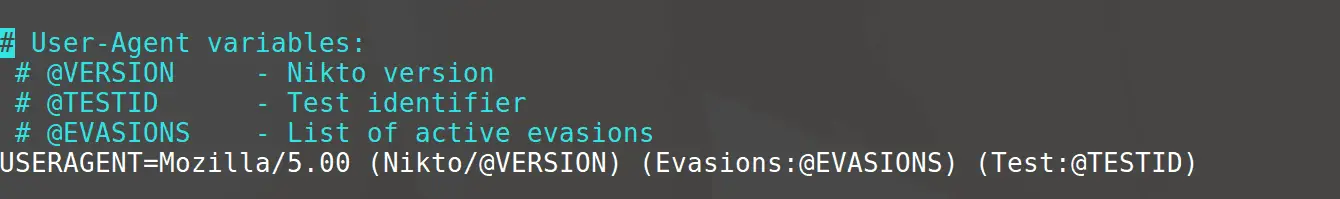
- Modify user agent
Comments
Post a Comment